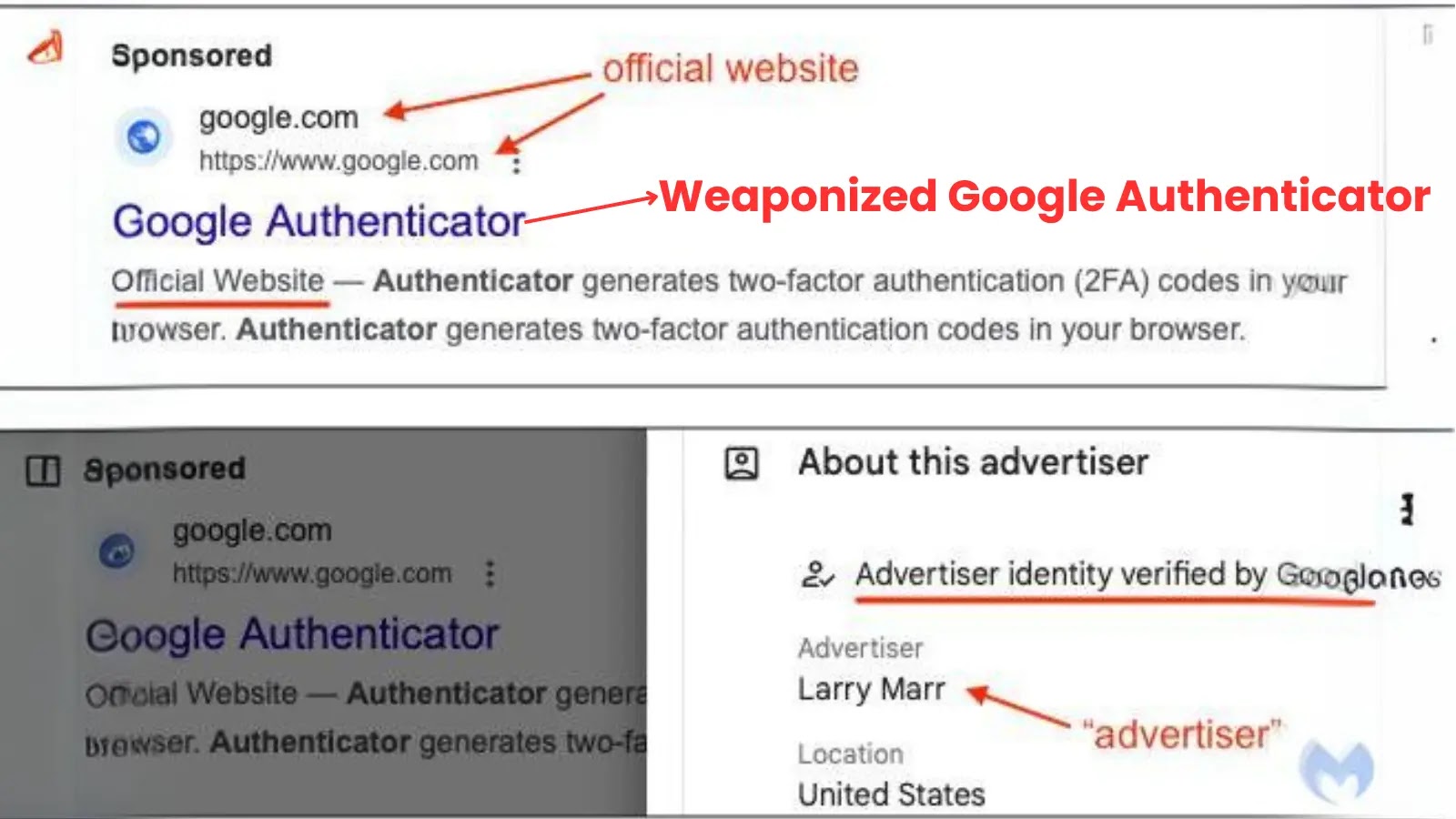
In recent days, threat actors have leveraged the popular Google Authenticator (a multi-factor authentication program) through Google ads, infecting devices with malware.
In this instance, an unidentified person was able to pose as Google and effectively distribute malware that was tricked as a legitimate Google product.
This not only deceives innocent individuals into downloading malware or losing their personal information to phishing websites, but it also damages consumer confidence in companies and, indirectly, in Google Search.
How to Build a Security Framework With Limited Resources IT Security Team (PDF) - Free Guide
Posing As Google via Fake Ad For Authenticator
Researchers say the main cause of brand impersonation is advertisements that seem to be from legitimate sources and have Google-verified advertising identities.

Larry Marr, in this instance, is most likely a fake account that has nothing to do with Google.
However, researchers noticed that there were multiple redirects via attacker-controlled intermediary sites prior to reaching the fake Authenticator website.
On the same day that the ad appeared, NICENIC INTERNATIONAL GROUP CO., LIMITED registered the fake site chromeweb-authenticators[.]com.
Reports say we can view the code that downloads Authenticator.exe from GitHub by examining the website’s source code.
.webp)
The threat actor can leverage a reliable cloud resource by hosting the file on GitHub, which is unlikely to be prevented using traditional methods.
Even though GitHub is the official software repository, not all scripts or apps housed there are reliable.
The threat actor created under the account authe-gogle, creating the authgg repository that includes the malicious Authenticator.exe.
“Looking at the file itself, we can see that it has been digitally signed by “Songyuan Meiying Electronic Products Co., Ltd.” just one day before, and the signature is still valid at the time of writing”, reports MalwareBytes Labs.
Researchers identify the payload as a DeerStealer, a type of stealer that uses a website located at vaniloin[.]fun under the control of the attacker to obtain and exploit your personal information.
It is worth mentioning that Google Authenticator is a widely recognized and reliable multi-factor authentication application.
Therefore, it is a bit surprising that potential victims could be compromised while attempting to strengthen their security measures.
Hence, it is advised to visit the official repositories directly rather than clicking on advertisements to download any form of software.
Indicators Of Compromise
Malicious domains
.webp)
Are you from SOC and DFIR Teams? – Analyse Malware Incidents & get live Access with ANY.RUN -> Free Access