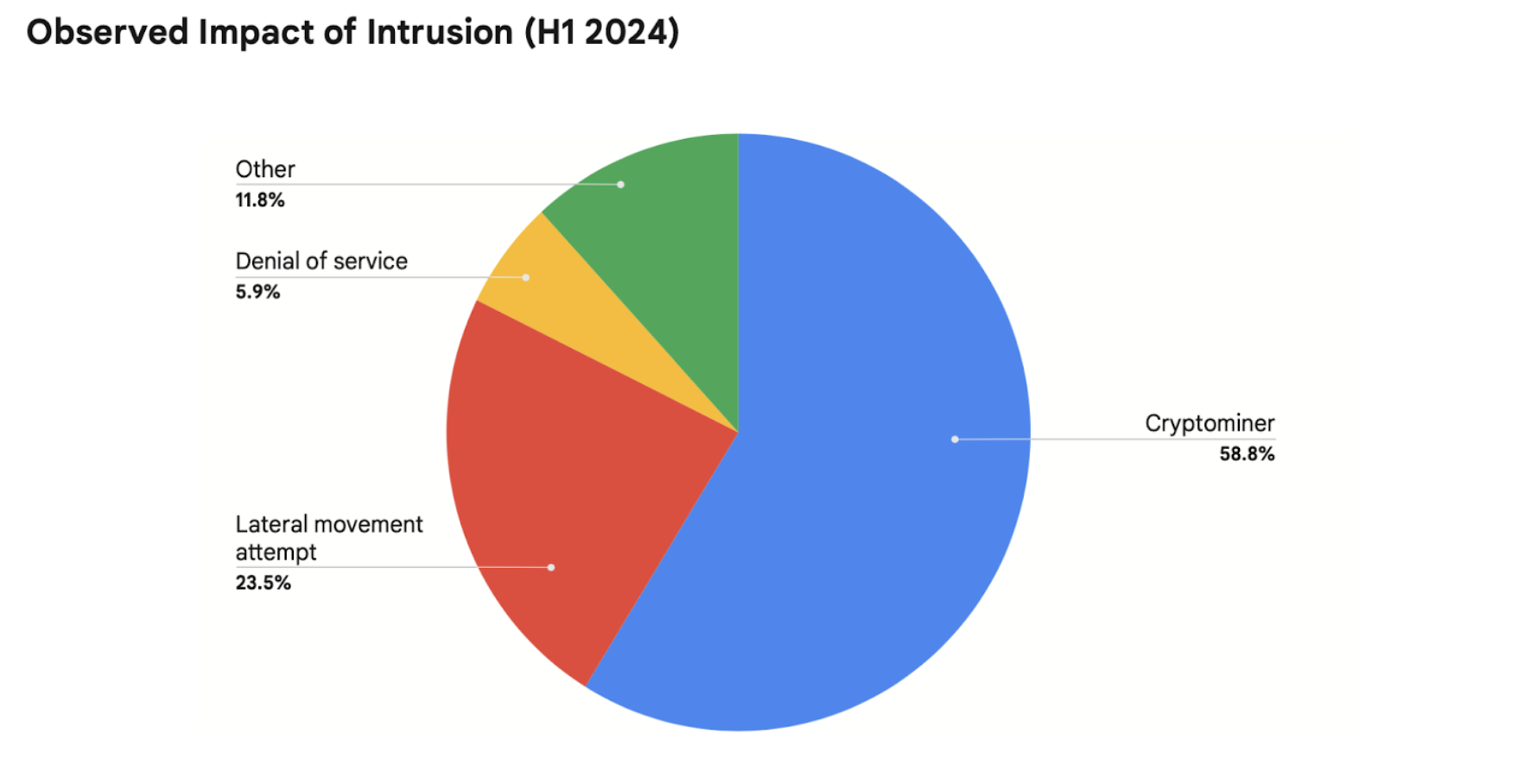
The Google Threat Horizons report examined initial intrusions for the first half of 2024 and found, from the case studies examined, that cloud computing services are facing increasing threats of compromise and abuse. The same advantages that serverless computing provides for legitimate organizations have proven attractive for threat actors as they leverage illegitimate access in order to deploy endpoints that manage their own malware processes and host credential phishing pages. A vast majority (~60%) of actions on objective have been spinning up parasitic crypto-mining operations leveraging the victims’ resources followed by attempting lateral movement (~24%). Both activities potentially being quite costly to preserve the Confidentiality, Integrity, and Availability of organizational assets.
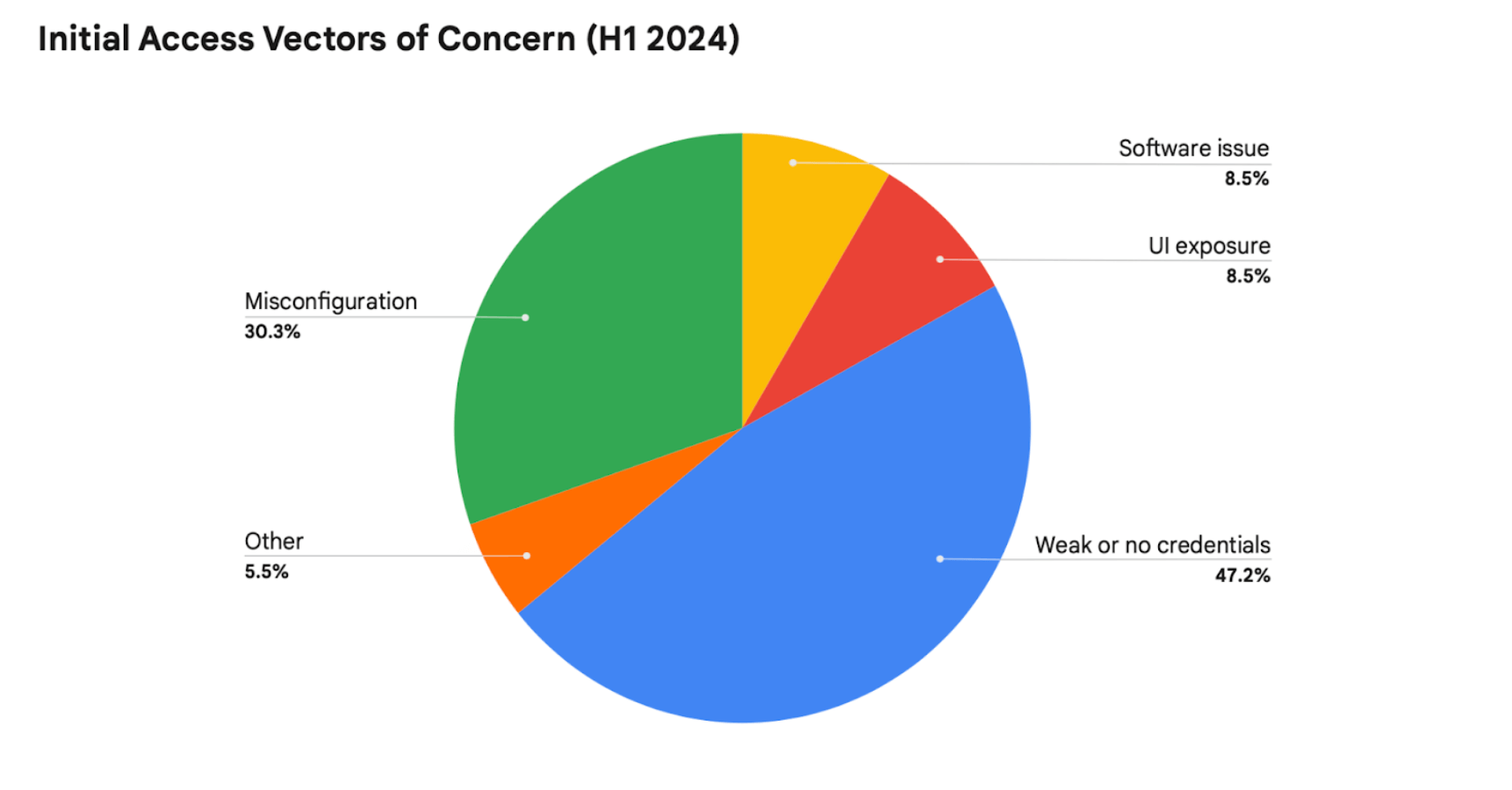
Weak, Compromised, or non-existent credentials have proven time and time again to be the most effective intrusion technique. From the point of view of an attacker, why break a window when you’ve got the keys to the castle? The findings of the Google Threat Horizons report show almost 50% of initial footholds were gained by abusing valid credentials that were compromised or non-existent. The next most prevalent initial access has been observed to be misconfiguration at 30%. These figures allow us as security practitioners to assess what areas are most vulnerable, and to account for the common behaviors of these threat actors.
Administrators concerned with their defensive posture can be proactive by ensuring systems are configured properly, that least privilege rules are implemented and red teaming is put in place. Additionally scanning environments for malware, and suspicious user behavior to alert for malware and other malicious services and activities. With the rise of infostealer malware, it is important, now more than ever, to put in place strong password policies and implement robust compromised credential monitoring.
AUTHOR
 Amos Struthers
Amos Struthers
Amos is a member of the threat research team, dedicated to identifying and cultivating sources and actionable intelligence for Enzoic products. He enjoys learning about new attack vectors, exploits, and vulnerabilities, as well as those threat actors who are utilizing them in the wild. When not at work, Amos loves spending time with his family, cooking, lifting weights, and competing in various shooting sports.
*** This is a Security Bloggers Network syndicated blog from Blog | Enzoic authored by Enzoic. Read the original post at: https://www.enzoic.com/blog/google-threat-horizon-analysis/