Google has fixed two vulnerabilities that, when chained together, could expose the email addresses of YouTube accounts, causing a massive privacy breach for those using the site anonymously.
The flaws were discovered by security researchers Brutecat (brutecat.com) and Nathan (schizo.org), who found that YouTube and Pixel Recorder APIs could be used to obtain user’s Google Gaia IDs and convert them into their email addresses.
The ability to convert a YouTube channel into an owner’s email address is a significant privacy risk to content creators, whistleblowers, and activists relying on being anonymous online.
Leaky APIs
The first part of the attack chain, which was exploitable for months, was discovered after BruteCat looked through Google’s Internal People API and found that Google’s network-wide “blocking” feature required an obfuscated Gaia ID and a display name.
A Gaia ID is a unique internal identifier Google uses to manage accounts across its network of sites. As users register for a single “Google Account” that is used across all of Google’s sites, this ID is the same throughout Gmail, YouTube, Google Drive, and other Google services.
However, this ID is not meant to be public and is for internal use to share data between Google’s systems.
Playing around with the blocking feature on YouTube, BruteCat discovered that when attempting to block someone in a live chat, YouTube exposes the targeted person’s obfuscated Gaia ID in a response from the /youtube/v1/live_chat/get_item_context_menu API request.
The response included base64 encoded data that, when decoded, contained the Gaia ID of that user.
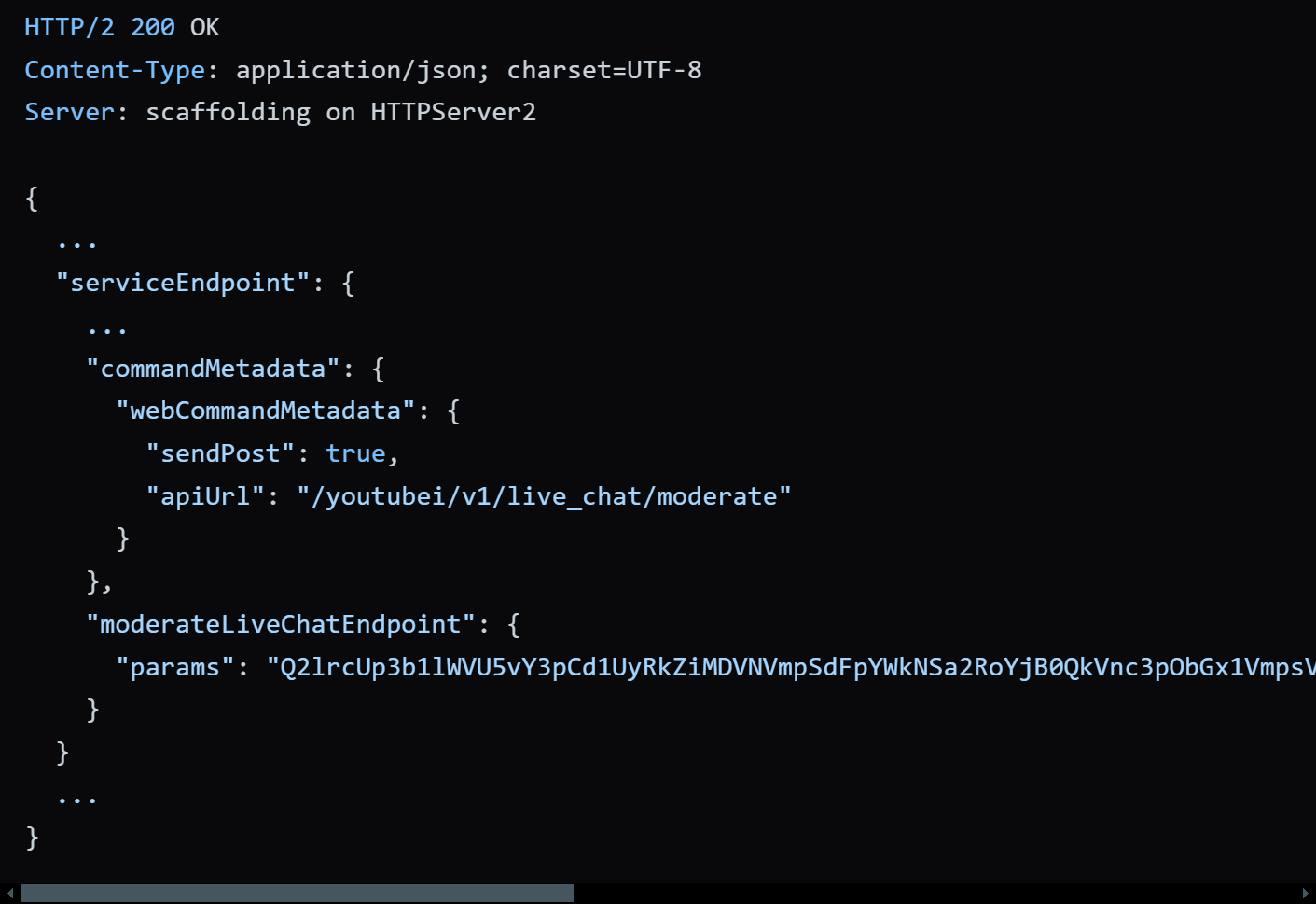
The researchers found that simply clicking on the three-dot menu in a chat triggered a background request to YouTube’s API, allowing them to access the ID without having to block them. By modifying the API call, the researchers retrieved the Gaia ID of any YouTube channel, including those attempting to remain anonymous.
Armed with the Gaia ID, they now wanted to figure out a way to convert it into an email address, which would increase the flaw’s severity.
However, older APIs that could do this have been deprecated or no longer work, so BruteCat and Nathan began looking for old, outdated Google services that could potentially still be exploited.
After experimenting, Nathan discovered that Pixel Recorder has a web-based API that could be used to convert the ID into an email when sharing a recording.
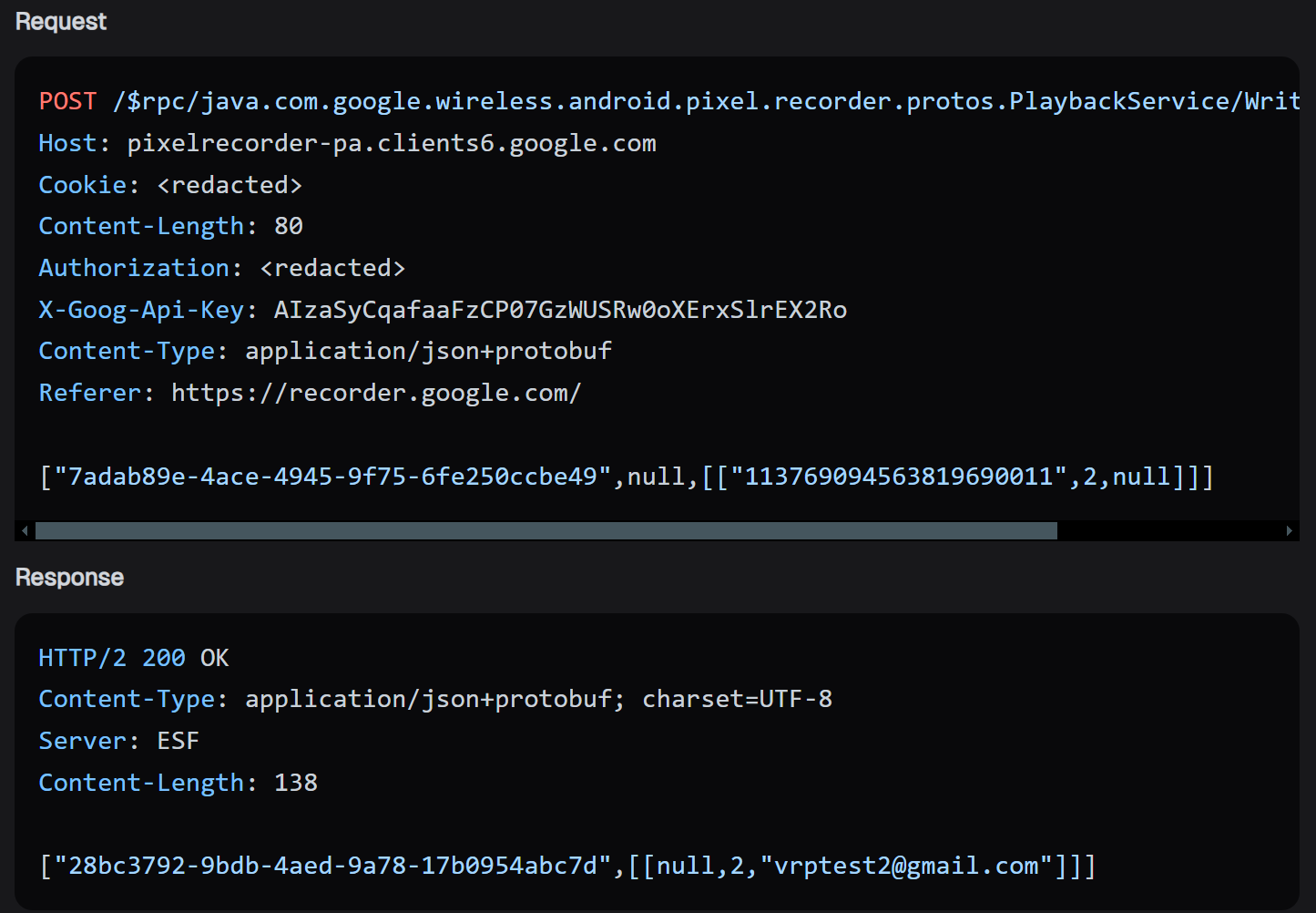
This meant that once a YouTube user’s Gaia ID was obtained, it could be submitted to the Pixel Recorder sharing feature, which then returned the associated email address, potentially compromising the identity of millions of YouTube users.
“Gaia IDs are leaked across several Google products apart from just YouTube (Maps, Play, Pay), causing a significant privacy risk for all Google users, as they can be used to reveal the email address tied to the Google account,” the researchers told BleepingComputer.
While the researchers now had a way of getting an email address from Gaia ID, the service also notified the users of the shared file, potentially alerting them of the malicious activity.
As the notification email included a video’s title in the email notification, the researchers modified their request to include millions of characters in the title data, which caused the email notification service to fail and not send the email.
The researchers disclosed the flaw to Google on September 24th, 2024, and it was ultimately fixed last week on February 9th, 2025.
Google initially responded that the vulnerability was a duplicate of a previously tracked bug, only awarding a $3,133 bounty. However, after demonstrating the additional Pixel Recorder component, they increased the bounty to $10,633, citing a high likelihood that it would be exploited.
BruteCat and Nathan told BleepingComputer that Google mitigated the bugs by fixing the Gaia ID leak and the Gaia ID to Email flaw via Pixel Recorder. Google also made it so blocking a user on YouTube only impacted that site and would not affect other services.
Google has confirmed to BleepingComputer that mitigations for the bugs are now completed and that there are no signs that any attacker actively exploited the flaws.

