This is my completely informal, uncertified, unreviewed and otherwise completely unofficial blog inspired by my reading of our next Threat Horizons Report (full version) that we just released (the official blog for #1 report, my unofficial blogs for #2, #3, #4, #5, #6, #7, #8 and #9).
My favorite quotes from the report follow below:
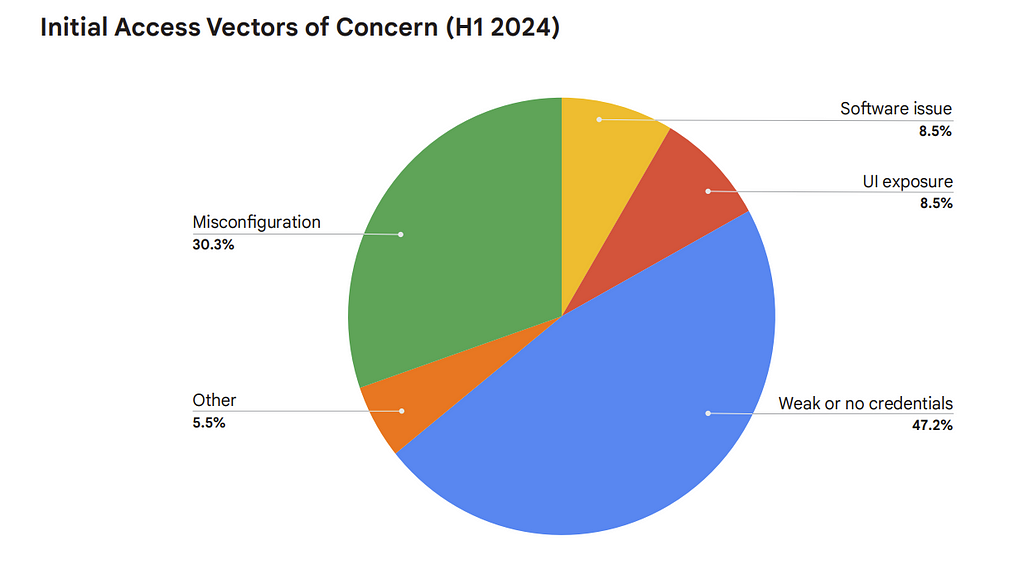
- “Weak or no credentials remained a key driver of initial access, accounting for the most frequent successful vector and the second most commonly seen trigger for detection rules. Misconfiguration, however, jumped to over 30%, largely due to the high volume of detections of misconfigured or poorly configured environmental factors. ” [A.C. — how cloud environments get owned does not change much. The main news here is that there is no news…]
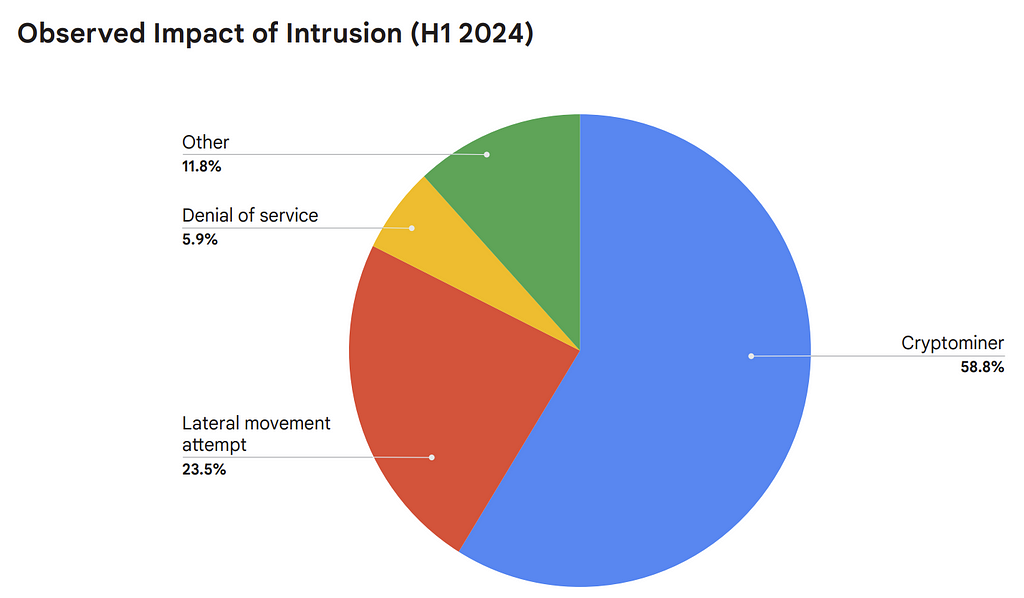
- “End goals of intrusions largely remained the same over H1 2024, as nearly 59% of intrusions were motivated by cryptomining efforts, which is slightly ower than our observations from H2 2023 (65%).” [A.C. — crypto remains a decent business for criminals, but I perhaps should not resort to tautology … I already said crypto so saying criminals is redundant 🙂]
- “Ensure full adoption of multifactor authentication (MFA) for administrative access to serverless web apps as well as other Google Cloud instances. ” [A.C. — shocking advice, would you agree? BTW, this also helps vs the miners.]
- “Throughout the course of incident response and proactive engagements during the last two years, Mandiant has observed a multitude of threats to serverless architecture across all cloud providers. The following threats should be top-of-mind when deploying or operating serverless architecture:
- Hard-coded and clear-text secrets
- Attackers utilizing serverless infrastructure for malicious purposes
- Insecure architecture and development practices
- Misconfigured backend services” [A.C. — this is just pure gold! No comments needed, use it! This also matches the 1st pie chart: creds and misconfigs is what gets you in the cloud! Ah, and also AD, that one is a real killer!]
- “Threat actors utilize serverless runtime environments by employing them either as a proxy for traffic destined to an adversary-controlled infrastructure or by directing traffic directly to the compromised machine” [A.C. — so, yes, the attackers learned serverless, why didn’t you?!]
- “Following Google’s disruption of their scaled abuse campaigns, they [PINEAPPLE] attempted to continue abusing Cloud Run intermittently at lower volumes. […] Threat actors abusing cloud services shift their tactics in response to defenders’ detection and mitigation measures. “ [A.C. — reminder: this is why security is fun!]
Now, go and read the report!
Related posts:
Google Cloud Security Threat Horizons Report #10 Is Out! was originally published in Anton on Security on Medium, where people are continuing the conversation by highlighting and responding to this story.
*** This is a Security Bloggers Network syndicated blog from Stories by Anton Chuvakin on Medium authored by Anton Chuvakin. Read the original post at: https://medium.com/anton-on-security/google-cloud-security-threat-horizons-report-10-is-out-bd1d1f7b56bd?source=rss-11065c9e943e——2