Security researchers revealed this week that a critical remote code execution (RCE) vulnerability in Google Cloud Platform (GCP) could have allowed attackers to run malicious code on millions of Google’s servers.
The flaw, dubbed “CloudImposer” by Tenable Research, has since been patched by Google.
The vulnerability was discovered in GCP’s Cloud Composer service, a managed workflow orchestration tool based on Apache Airflow. It stemmed from a risky package installation process that left the service open to dependency confusion attacks.
Tenable researchers found that Google was using the “–extra-index-url” argument when installing private Python packages in Cloud Composer. This argument instructs the package manager to check both private and public repositories, potentially allowing attackers to trick it into installing malicious packages from public sources.
Decoding Compliance: What CISOs Need to Know – Join Free Webinar
“CloudImposer could have allowed attackers to conduct a massive supply chain attack by compromising the Google Cloud Platform’s Cloud Composer service for orchestrating software pipelines,” said Liv Matan, a security researcher at Tenable.
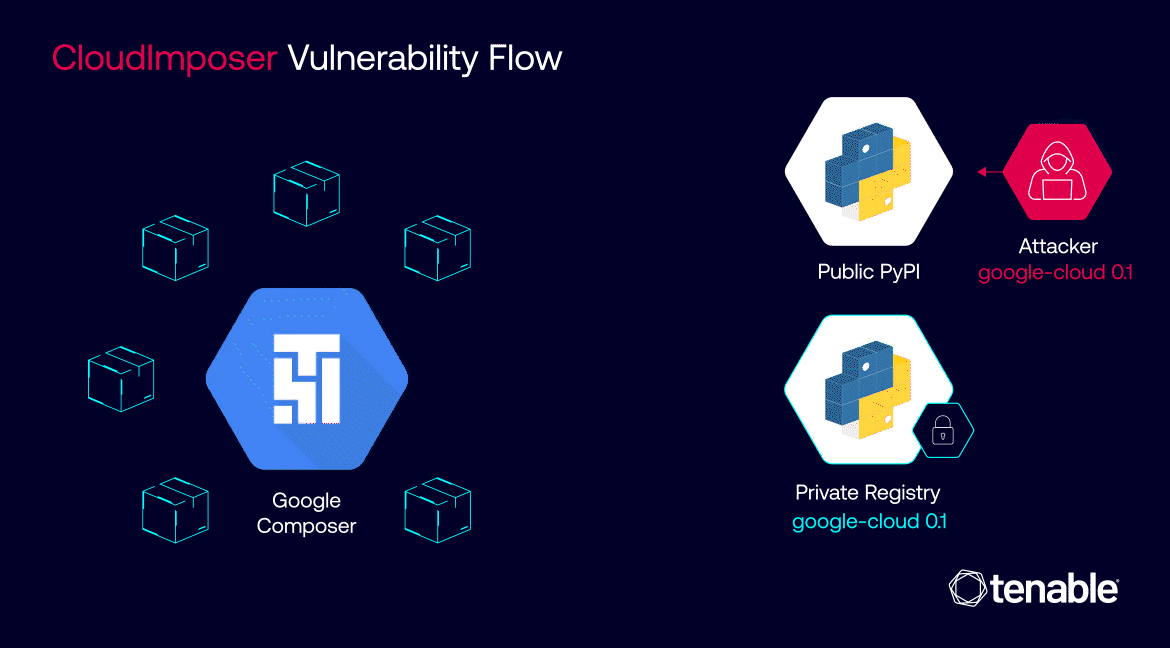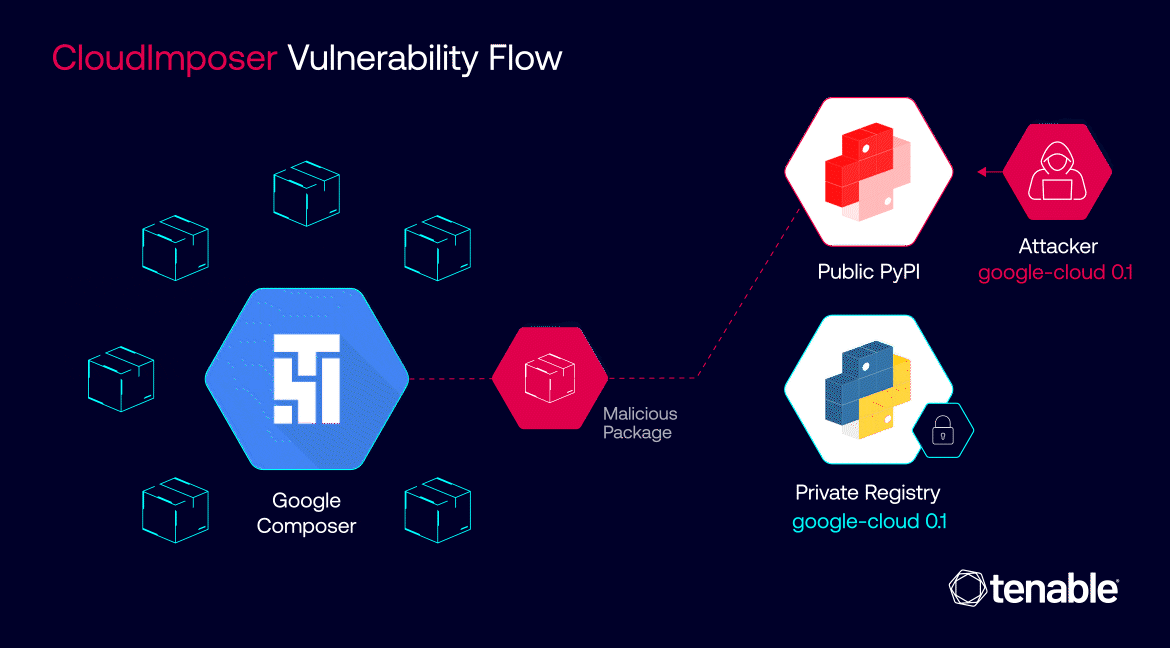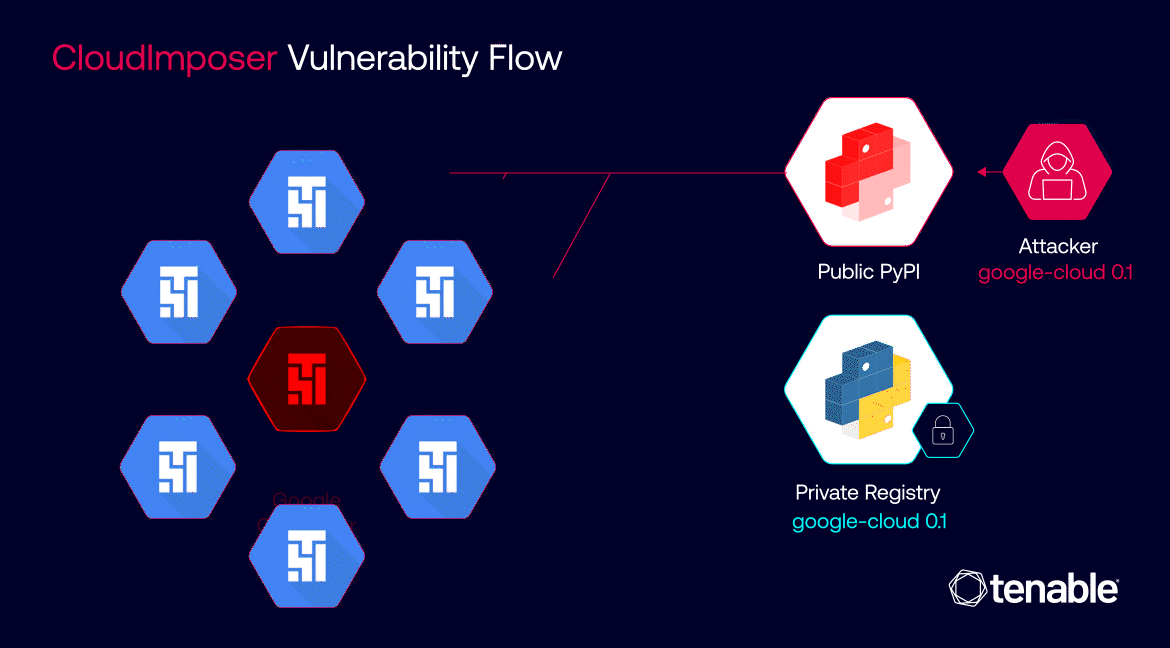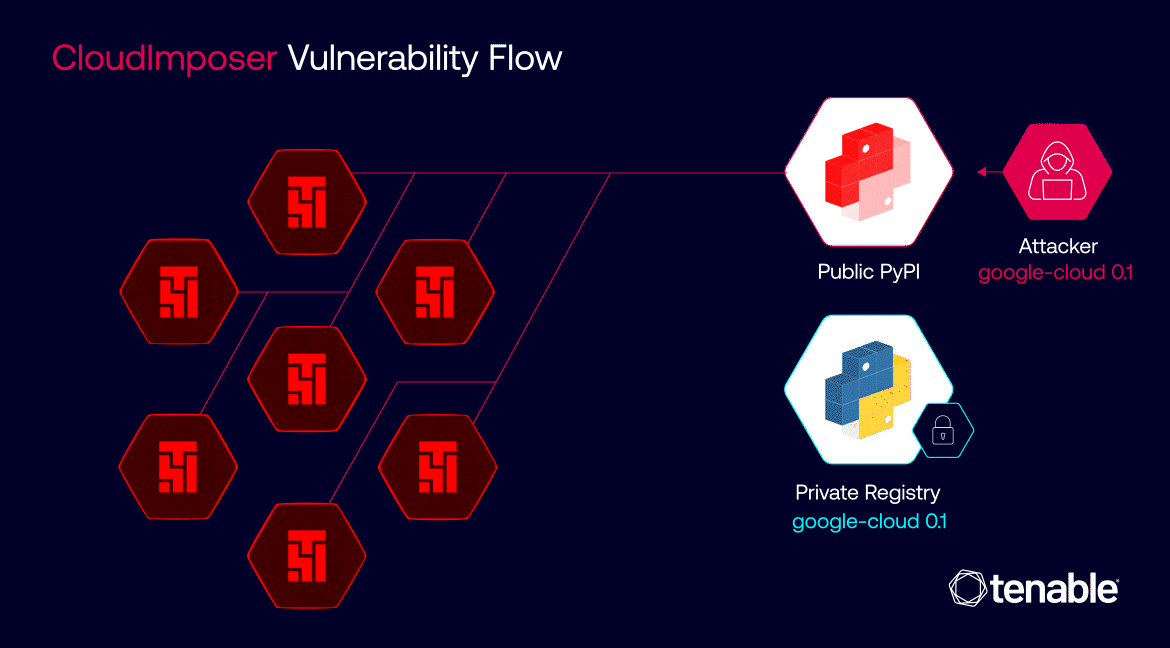
The flaw affected multiple GCP services including App Engine, Cloud Functions, and Cloud Composer. By exploiting it, an attacker could have uploaded a malicious package to the public PyPI repository that would then be automatically installed on Cloud Composer instances with elevated permissions.
This could have given attackers the ability to execute arbitrary code, steal service account credentials, and potentially move laterally to compromise other GCP services.
The widespread nature of the vulnerability meant that a single compromised package could have impacted millions of servers across Google’s infrastructure and its customers’ environments.
“Supply chain attacks in the cloud are exponentially more harmful than on premises,” Tenable noted. “One malicious package in a cloud service can be deployed to – and harm – millions of users.”
Google has since fixed the vulnerability by ensuring the affected Python package is only installed from a private repository. The company also implemented additional safeguards, including checksum verification, to validate package integrity.
In response to the findings, Google has updated its documentation to recommend using the safer “–index-url” argument instead of “–extra-index-url” when installing packages. The company also advises customers to use GCP’s Artifact Registry virtual repository to manage multiple package sources.
The discovery highlights ongoing challenges in securing cloud environments and software supply chains. It also underscores the need for both cloud providers and customers to implement robust security practices around package management and dependency resolution.
Organizations using GCP services are advised to review their package installation processes and ensure they have appropriate safeguards in place to prevent dependency confusion attacks. This includes using version pinning, checksums, and private repositories where possible.
The CloudImposer vulnerability serves as a reminder of the complex, interconnected nature of modern cloud environments and the potential for seemingly small misconfigurations to have far-reaching security implications. As cloud adoption continues to grow, addressing these types of supply chain risks will remain a critical priority for the industry.
Are You From SOC/DFIR Teams? - Try Advanced Malware and Phishing Analysis With ANY.RUN - 14-day free trial


