Google Calendar is a tool for organizing schedules and managing time, designed to assist individuals and businesses in planning their days efficiently. According to Calendly.com, Google Calendar is used by more than 500 million people and is available in 41 different languages.
Due to Google Calendar’s popularity and efficiency in everyday tasks, it is no wonder it has become a target for cyber criminals. Recently, cyber security researchers at Check Point, have observed cyber criminal manipulation of dedicated Google tools – namely Google Calendar and Google Drawings. Many of the emails appear legitimate because they appear to directly originate from Google Calendar.
Cyber criminals are modifying “sender” headers, making emails look as though they were sent via Google Calendar on behalf of a known and legitimate individual. Roughly 300 brands have been affected by this campaign thus far, with cyber researchers observing over 4,000 of these phishing emails in a four week period.
Threat Overview
As noted previously, these phishing attacks initially exploited the user-friendly features inherent in Google Calendar, with links connecting to Google Forms.
However, after observing that security products could flag malicious Calendar invites, cyber criminals evolved the attack to align with the capabilities of Google Drawings.
Cyber Criminal Motives
At the heart of this campaign, cyber criminals aim to fool users into clicking on malicious links or attachments that allow for the theft of either corporate or personal information.
After an individual unwittingly discloses sensitive data, the details are then applied to financial scams, where cyber criminals may engage in credit card fraud, unauthorized transactions or similar, illicit activities. The stolen information may also be used to bypass security measures on other accounts, leading to further compromise.
For both organizations and individuals, these types of scams can prove extremely stressful, with long-term, deleterious effects.
Attack Execution Techniques
As noted previously, the initial emails include a link or the calendar file (.ics) with a link to Google Forms or Google Drawings.
Users are then asked to click on another link, which is often disguised as a fake reCAPTCHA or support button.
After clicking on the link, the user is forwarded to a page that looks like a cryptocurrency mining landing page or bitcoin support page.
These pages are actually intended to perpetrate financial scams. Once users reach said page, they are asked to complete a fake authentication process, enter personal information, and eventually provide payment details.
The phishing attack shown below initially began with a Google Calendar invite. Some of the emails do really look like calendar notifications, while others use a custom format:
Initial phishing attack email example
If the guests were known contacts, a user might believe the ruse, as the rest of the screen looks relatively ordinary:
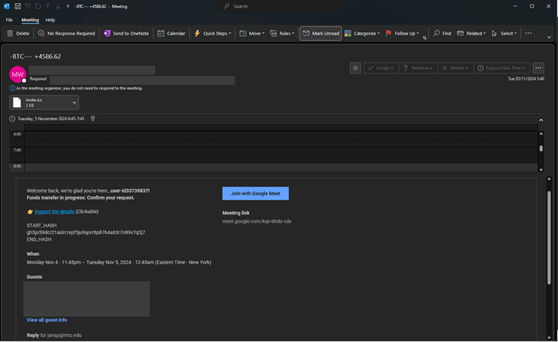
Google Calendar set-up
Blocking This Attack
For organizations that want to safeguard users from these types of phishing threats and others, consider the following practical recommendations:
- Advanced email security solutions. Solutions like Harmony Email & Collaboration can effectively detect and block sophisticated phishing attempts – even when they manipulate trusted platforms, like Google Calendar and Google Drawings.
High-caliber email security solutions include attachment scanning, URL reputation checks, and AI-driven anomaly detection. - Monitor the use of third-party Google Apps. Leverage cyber security tools that can specifically detect and warn your organization about suspicious activity on third-party apps.
- Implement strong authentication mechanisms. One of the most important actions that security administrators can take consists of implementing Multi-Factor Authentication (MFA) across business accounts.
Further, deploy behavior analytics tools that can detect unusual login attempts or suspicious activities, including navigation to cryptocurrency-related sites.
For individuals who are concerned about these scams reaching their personal inboxes, consider the following practical recommendations.
- Remain wary of fake event invites. Does the invite have unexpected information on it or request that you complete unusual steps (i.e., CAPTCHA)? If so, avoid engaging.
- Carefully examine incoming content. Think before you click. Hover over links and then type the URL into Google for the purpose of accessing the website – a safer approach than otherwise.
- Enable two-factor authentication. For Google accounts and other repositories of sensitive information, enable two-factor authentication (2FA). If your credentials are compromised, 2FA can prevent criminals from accessing a given account.
When asked for comment, Google stated, “We recommend users enable the “known senders” setting in Google Calendar. This setting helps defend against this type of phishing by alerting the user when they receive an invitation from someone not in their contact list and/or they have not interacted with from their email address in the past.”
In 2025, upgrade your email security solution. Speak with an expert today and get a Harmony Email & Collaboration demo.

