Criminals constantly develop new ways to scam people, and their latest tactic involves infecting Android phones with malware to access banking information and other details. Researchers at the cybersecurity firm Cyble have discovered a new malware, dubbed Antidot, which masquerades as a Google Play update application. It displays fake Google Play update pages in multiple languages and captures sensitive information.
GET SECURITY ALERTS, EXPERT TIPS – SIGN UP FOR KURT’S NEWSLETTER – THE CYBERGUY REPORT HERE
A man looking at his Android phone (Kurt “CyberGuy” Knutsson)
How does this malware enter your Android?
As detailed by Cyble, Antidote is a Trojan – malware that misleads users of its true intent by disguising itself as a standard program. In this case, it impersonates the Google Play Store (the default app market for downloading and updating apps on Android phones) and captures your important data.
Antidot enters your Android phone by tricking you into sideloading it as an APK (Android Package Kit). APK is the file format that Android uses to distribute and install applications. When you sideload an app, you’re manually installing an APK file on your Android device, which is not obtained through the Google Play Store. You won’t find it on the Play Store because Google makes sure to keep most of the malicious apps off its platform. However, you may come across it on third-party app stores or other less legitimate sources.
The malware can also enter your phone through phishing emails and text messages. For example, you might receive an email claiming you’ve won something (a lottery, a phone, etc.). You open the email and click on the link, and either nothing happens or you are taken to a dummy site. However, malware has been downloaded and installed on your phone.

A man on his Android phone (Kurt “CyberGuy” Knutsson)
VOICE CLONING IS THE NEW WEAPON IN SCAMMERS’ ARSENAL FOR FAMILY EMERGENCY SCHEMES
How does the Antidot trojan work?
Once the malware is installed on your Android phone, it displays a fake update page featuring a “Continue” button that takes you to the Accessibility settings. Antidot relies on the Accessibility services to carry out its malicious activities as they allow it to gain complete control over your phone.
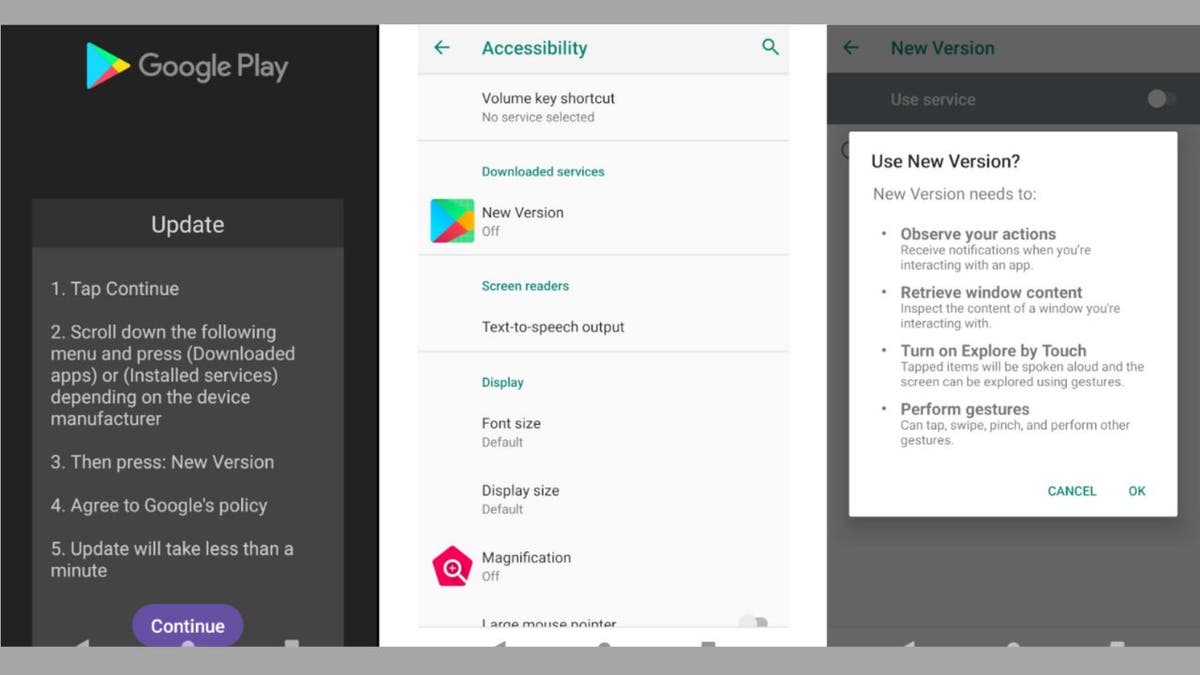
Fake Google Play update page (Cyble) (Kurt “CyberGuy” Knutsson)
The trojan displays fake update pages in various languages, including German, French, Spanish, Russian, Portuguese, Romanian and English, indicating that it is targeting Android users in these language-speaking regions.
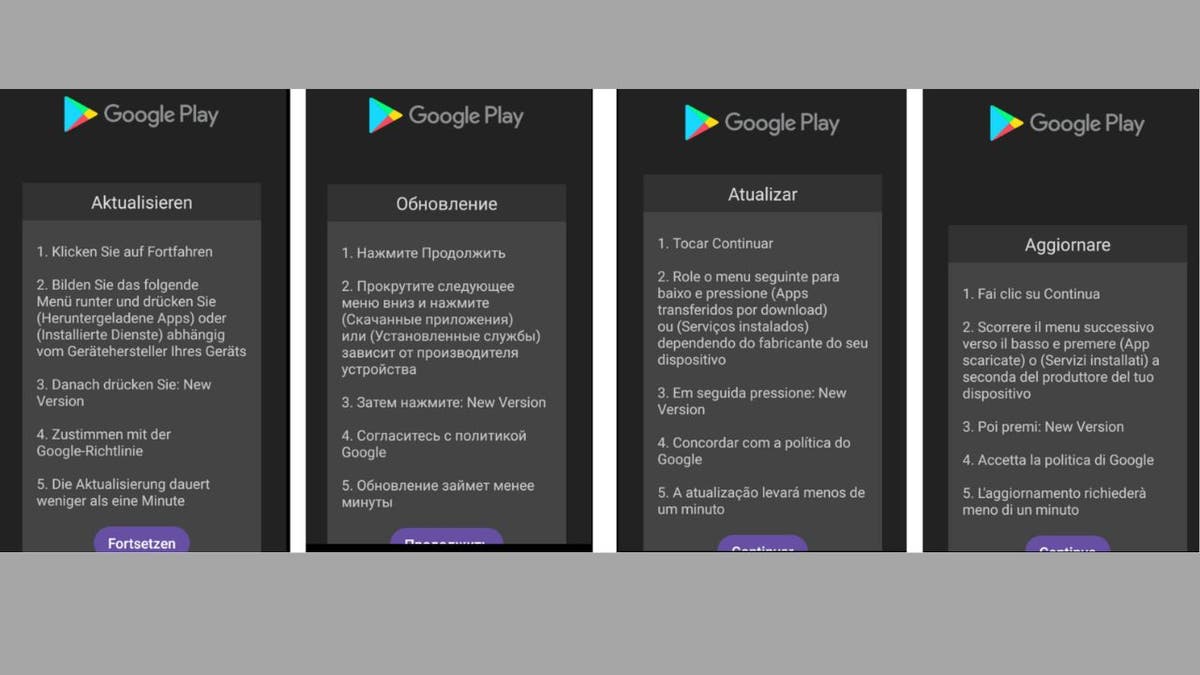
Fake Google Play update pages in different languages (Cyble) (Kurt “CyberGuy” Knutsson)
SUBSCRIBE TO KURT’S YOUTUBE CHANNEL FOR QUICK VIDEO TIPS ON HOW TO WORK ALL OF YOUR TECH DEVICES
After gaining access to your phone’s accessibility settings, it can access whatever information it wants, whether it’s collecting contacts and text messages, harvesting credentials, locking and unlocking the device, or forwarding calls.
To steal passwords and other credentials, Antidot uses a sneaky trick called an overlay attack. When you open your bank app on your phone, the malware loads a fake website that looks exactly like the real bank app and covers it up. When you type in your login details, the hackers capture them, and they can then steal your money, commit fraud or even steal your identity with enough information.
If the malware doesn’t have a fake website for an app, it uses another trick called “keylogging,” which captures everything you type on your Android smartphone, including your passwords.

A hacker working off of various computer screens (Kurt “CyberGuy” Knutsson)
‘UNSUBSCRIBE’ EMAIL SCAM IS TARGETING AMERICANS
10 ways you can protect yourself from the Android banking trojan
While a trojan is hard to detect and can be dangerous once it enters your phone, there are several things you can do to protect your data.
1) Be cautious of phishing attempts: Be vigilant about emails, phone calls or messages from unknown sources asking for personal information. Avoid clicking on suspicious links or providing sensitive details unless you can verify the legitimacy of the request.
2) Have strong antivirus software: Android has its own built-in malware protection called Play Protect, but it’s not enough to stop all malicious software. Historically, Play Protect hasn’t been 100% foolproof at removing all known malware from Android phones. The best way to protect yourself from clicking malicious links that install malware that may get access to your private information is to have antivirus protection installed on all your devices. This can also alert you of any phishing emails or ransomware scams. Get my picks for the best 2024 antivirus protection winners for your Windows, Mac, Android & iOS devices.
3) Download apps from reliable sources: It’s important to download apps only from trusted sources like the Google Play Store. They have strict checks to prevent malware and other harmful software. Avoid downloading apps from unknown websites or unofficial stores, as they can pose a higher risk to your personal data and device.
4) Use an identity theft protection service: Identity theft companies can monitor personal information like your Social Security Number, phone number and email address and alert you if it is being sold on the dark web or being used to open an account. They can also assist you in freezing your bank and credit card accounts to prevent further unauthorized use by criminals. See my tips and best picks on how to protect yourself from identity theft.
5) Monitor your accounts: If you think you have been affected by the banking trojan, regularly review your bank statements, credit card statements and other financial accounts for any unauthorized activity. If you notice any suspicious transactions, report them immediately to your bank or credit card company.
6) Enable SMS notifications for your bank accounts: By enabling SMS notifications, you can monitor your accounts for any unauthorized transactions.
7) Set up two-factor authentication (2FA): 2FA is an extra shield that prevents hackers from accessing your accounts.
8) Use a password manager: A password manager can help you create and store strong, unique passwords for all your accounts, reducing the risk of password theft.
9) Regularly update your device’s operating system and apps: Keeping your software up to date is crucial as updates often include security patches for newly discovered vulnerabilities that could be exploited by trojans.
10) Be wary of granting permissions: Carefully review the permissions requested by apps. If an app asks for more access than it needs for its functionality, it could be a red flag.
ANDROID USERS AT RISK AS BANKING TROJAN TARGETS MORE APPS
Kurt’s key takeaways
Staying one step ahead of cybercriminals is a constant challenge. The emergence of the Antidot trojan is a stark reminder that our vigilance must be as innovative as the threats we face. It’s not just about safeguarding our devices; it’s about protecting our digital existence. Remember, the power to prevent such intrusions largely rests in our hands. By adopting the protective measures outlined, from scrutinizing every app’s permissions to embracing robust security solutions, we can fortify our digital fortresses. Let’s not make it easy for the scammers.
In what ways do you think technology companies could improve their security measures to better protect users from malware like Antidot? Let us know by writing us at Cyberguy.com/Contact.
For more of my tech tips and security alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter.
Ask Kurt a question or let us know what stories you’d like us to cover.
Follow Kurt on his social channels:
Answers to the most asked CyberGuy questions:
Copyright 2024 CyberGuy.com. All rights reserved.

